Trickbot Campaign – Using the BLM Movement to Lure Victims
On June 10th, FortiGuard Labs discovered a malicious spam campaign that is taking advantage of the current “Black Lives Matter” protests in order to target users who may be sympathetic to the protests. The main goal of this campaign is to leverage users’ fear from the COVID-19 pandemic as well as the political strife currently running rampant throughout the United States in order to lure unsuspecting victims into downloading and opening malicious attachments.
This campaign utilizes a variety of subject lines for emails that contain malicious Microsoft Word documents as attachments in order to compel the user into interacting with the spam. The actual body content of the email is hastily written and contains multiple grammatical errors, but care is given to the actual subject line of the email.
The emails themselves contain variations in subjects and sender names to either circumvent spam filters or to simply create confusion. For examples of subject lines and senders, see the image below.
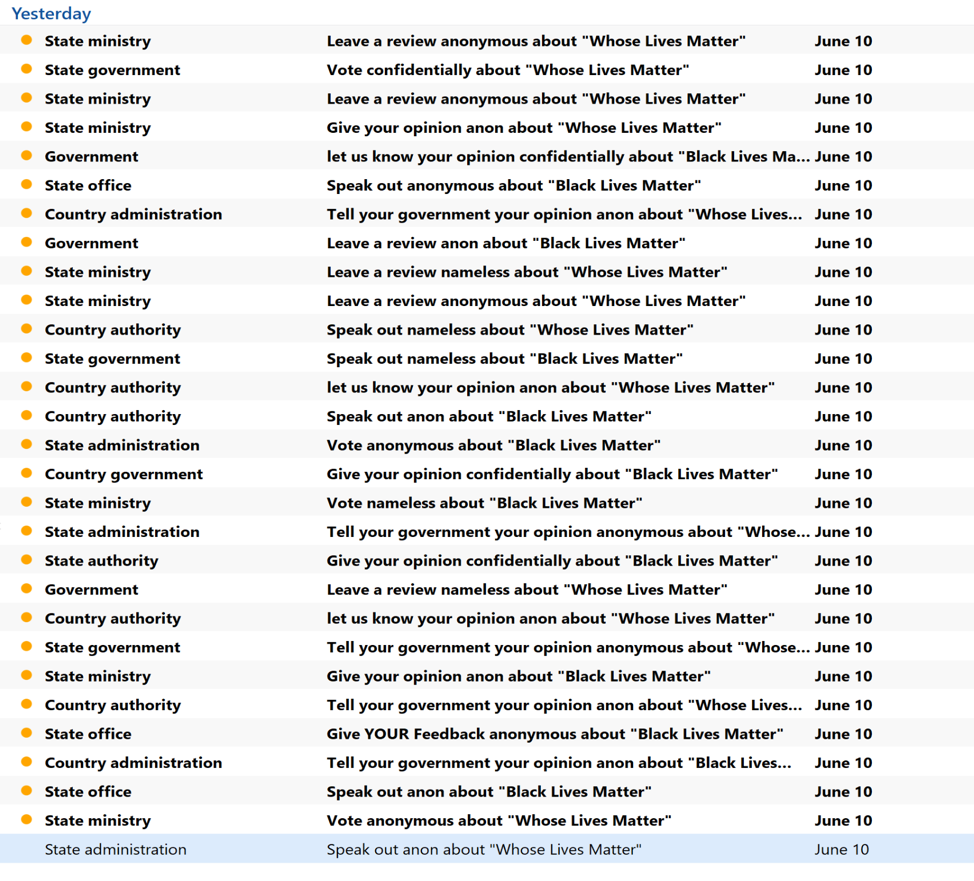
Courtesy of Fortinet.com
The malicious Word documents themselves follow a standard template that is written simply and entices the user to enable macros. The macros themselves are password protected, which is standard practice for malware developers used in attempt to prevent casual analysis or otherwise obfuscate their malicious intents. Upon malware execution, the malicious payload proceeds to contact command and control servers in order to download and execute the Trickbot malware. This current campaign itself follows closely to previous Trickbot campaigns that have leveraged the ongoing COVID-19 pandemic in order to lure victims into interacting with malicious email attachments.
The Trickbot malware is a well-known modular banking Trojan that can target sensitive information and can act as a dropper for other malware. The authors of this malware are continuously releasing new modules and version of the Trickbot malware in order to expand and refine its capabilities. Trickbot utilizes man-in-the-middle attacks to steal financial information, such as login credentials used during online banking. Some of Trickbot’s modules abuse the Server Message Block (SMB) protocol in order to spread the malware laterally across a network.
Through analysis of the domains and infrastructure used by this campaign’s actors it is found that they are all hosted within the Czech Republic but FortiGuard is quick to note that this proves little in terms of attribution. FortiGuard also claims that a thorough analysis of the passive DNS records shows no signs of past campaigns originating from the previously mentioned servers, which seems to be a trend thanks to the availability of “easy-to-spin-up” virtual private servers and on-demand cloud infrastructures.
To combat this growing trend of Trickbot campaigns, we recommend that all Antivirus and Intrusion Prevention System (IPS) definitions be kept up to date on a consistent basis and that organizations implement and follow a robust patch schedule when vendor updates become available. If patching is deemed not feasible, FortiGuard recommends that an IPS be utilized for proximity control, known as “virtual patching”, and that a risk assessment is conducted to determine additional mitigation safeguards within your environment.
Considering that the first stage of this malware campaign is to phish for victims, it is highly recommended that all organizations maintain a rigorous employee training program to continually educate their employees on the dangers of interacting with emails, links, and attachments that they receive from unknown parties. We encourage that your employees be trained to never open attachments from someone they don’t know and to always treat emails from unknown or untrusted parties with caution.
If you suspect that your network has been infected with the Trickbot malware, it is important to know that due to the spreading capabilities of the malware (thanks to the EternalBlue vulnerability), any infected machines on the network will re-infect machines that have been previously cleaned when they rejoin the network. It may be an arduous effort, but IT teams need to isolate, patch, and remediate each infected system one-by-one in order to fully cleans your network of Trickbot.
Sources
