Tracking Coronavirus/COVID19 Cyber Threat Campaigns
Last Updated Monday, March 30
This warning’s intent is to inform and create awareness with partners and customers of Atlas Cybersecurity. Malicious cyber attackers have wasted no time figuring out how to exploit the COVID-19 pandemic to execute phishing and deliver malware. Please be aware of the following examples of attacks that are being executed and remain vigilant in your online activities.
Vicious Panda: The COVID Campaign
A new campaign against the Mongolian public sector, which takes advantage of the current Coronavirus scare (aka COVID-19), in order to deliver a previously unknown malware implant to the targets. By tempting/tricking users to open documents which attackers embedded with malware, the attacker is able to exploit Microsoft Word vulnerabilities, an in turn deliver the malware. The attackers’ motive: to deliver malicious software and steal sensitive user information. Users should be wary of opening Microsoft Office documents from untrusted sources. (More technical details are available from Checkpoint Research at https://research.checkpoint.com/2020/vicious-panda-the-covid-campaign/)
Pakistan-based APT36
Thought to be nation-backed, APT36 has been active since 2016, possibly earlier, performing cyber espionage activity against Indian defense and government activities. The attackers send malicious office documents, pretending to be from the Government of India with a health advisory regarding Coronavirus. Victims are encouraged/tricked to enable macros, which executes the Crimson RAT Payload. The attackers now have control over the victim’s computer, and can steal sensitive information or install additional malware. Users should be suspicious of any Microsoft Office document that requests the user to enable macros. (More technical details are available from ThreatPost: https://threatpost.com/apt36-taps-coronavirus-as-golden-opportunity-to-spread-crimson-rat/153776/)
Bisonal Malware – an oldie but a goodie
Cybersecurity professionals have observed the dissemination of Bisonal Malware disguised as emergency contact information for Shincheonji (a South Korean-based megachurch, which reportedly has over 2000 members that have contracted COVID-19). Used as a backdoor to enable the attacker access to victims’ devices, Bisonal Malware has been identified attacking Korean institutions and companies since 2011. Users should always ensure their devices have up-to-date anti-malware software installed and active. (More details are available from ZDNet at https://www.zdnet.com/article/chinese-hackers-use-decade-old-bisonal-trojan-to-strike-russian-targets/)
Hancitor Malware
Developers behind the malicious downloader Hancitor malware are using the COVID-19 scare to target victims. Using COVID-19 themed malware purported to come from an insurance provider, the attacker tricks the user into downloading a zip file that contains a script that when launched executes malicious code that then follows traditional Hancitor malware activity. Hancitor is a trojan-type program which is designed to open backdoor for other malware. It could be used to install ransomware, keyloggers, Remote Access Trojans (RATs), cryptocurrency miners, etc. The attacker’s goal is to make money from the victim, oftentimes either by extorting money out of victims for access to their data, or by stealing sensitive information (for example passwords, credit card numbers, etc.). The attackers then attempt to monetize the stolen information through sale on the black market or by using it to commit other crimes. Users should be suspicious of any files that are downloaded through an email link, especially one they did not expect. If users receive an unexpected invoice via email, they should be immediately suspicious and should contact their IT support team (and not click links or open attachments in the email). (Technical details and removal instructions are available here: https://www.pcrisk.com/removal-guides/17293-covid-19-insurance-plan-from-cigna-email-virus)
Scam Texts
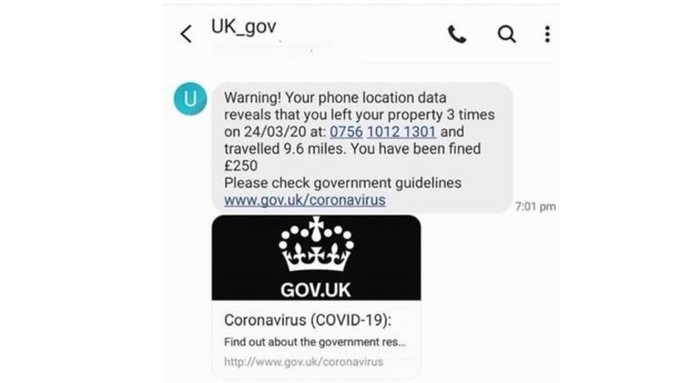
A series of scam texts have been sent to UK Citizens telling them they have been fined for violating lockdown and have been fined. If they follow the link, they are brought to a payment processor asking them to enter their credit card information. These so-called fines and this site have nothing to do with the UK government and once people hand over their credit card information it is charged repetitively.
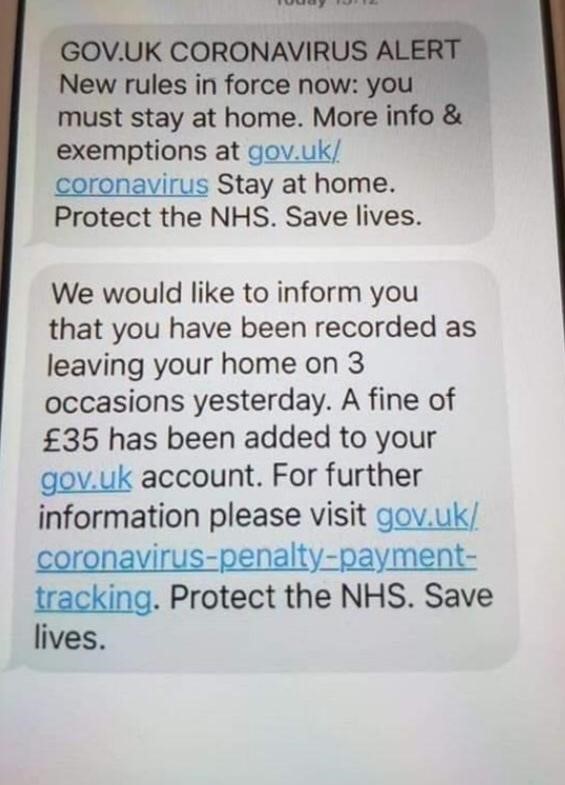
Netflix Scam Text
Scammers capitalized on the current social distancing recommendations and self-isolation orders by spreading around fake offers of free Netflix subscriptions. The website asks visitors to answer a few questions about how they are handling the COVID-19 pandemic, before telling them they have “won” and that they need to share the message with ten of their contacts in order to receive their free pass. The scammers will no doubt use these shared contacts to target in other scams. There does not appear to be any malicious payload or download associated with the campaign at this time, only intelligence gathering by malicious actors.

Ginp Banking Trojan introduces “CoronaVirus Finder”
A new campaign involving the Ginp banking trojan has surfaced that is redirecting users infected with the trojan to a web site offering to show the location of people infected with Corona virus for a very small fee. Once the user enters their credit card data, the scammers start making charges.
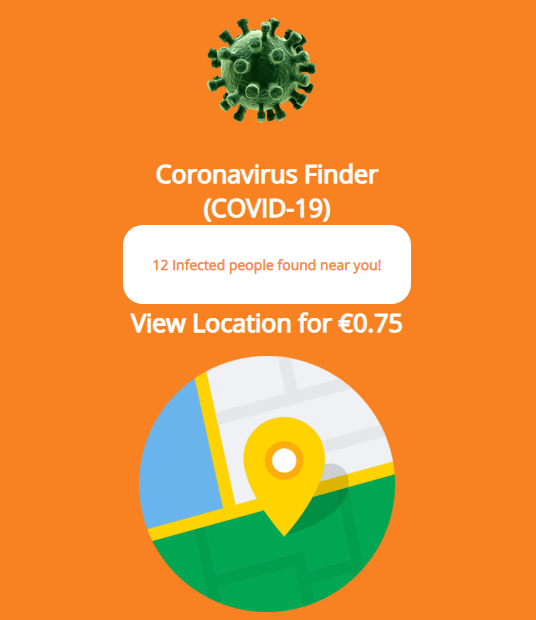
Source: https://www.kaspersky.com/blog/ginp-trojan-coronavirus-finder/34338/
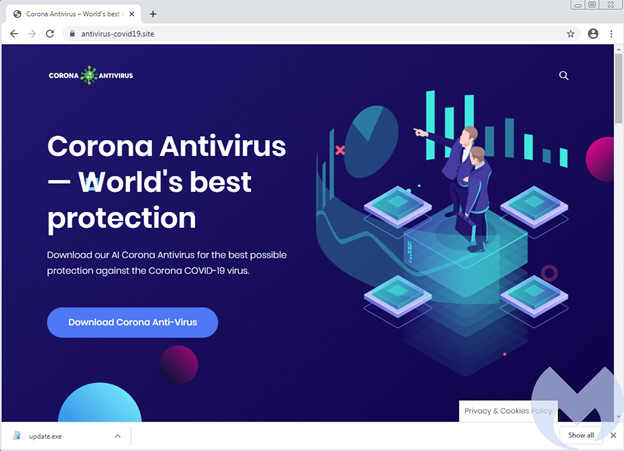
BlackNET RAT distributed by fake “Corona AV”
A spam campaign tricked users into visiting a “Corona Antivirus – World’s best protection” website where they tricked gullible users into downloading malware under the premise the antivirus software could prevent you from getting Corona Virus (COVID-19). They stated “Our scientists from Harvard University have been working on a special AI development to combat the virus using a windows app. Your PC actively protects you against the Coronaviruses (Cov) while the app is running.”
Free Safety Masks – Just Install This!
This scam works with malvertising which directs users to a malicious website that tells users they have won a free corona virus safety mask – all the must do is install an unsigned android application. Once installed, this application steals users contact information and sends out SMS messages on behalf of the user to all their contacts directing them to the same site. It provides the user with a button to click to enter shipping details for the mask, but the page does not load. In the future they may enter a fake credit card portal asking for money to cover the cost of shipping and handling.
Compromised Facebook Accounts Spreading Stimulus-Based Scam
Another text scam that has been observed by a local tv station in Ohio involves a ploy involving compromised Facebook accounts spreading the below message to contacts.
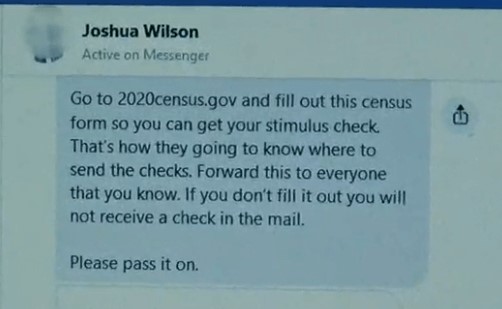
The message states you will not receive your stimulus from the U.S. government unless you complete your census form. The census has nothing to do with the stimulus plan. These attackers are using compromised Facebook accounts to try to trick people into providing their personal and/or financial information.
Additional Cases
- Cyber criminals are taking advantage of the Coronavirus pandemic. They are targeting victims with scams, malware campaigns, and other opportunistic attacks taking advantage of the chaos and fear to further their own malevolent agendas. According to a report by CheckPoint malware authors are even getting in on the action. They are selling discounted Exploit kits, malware, and miscellaneous exploit tools with a Coronavirus flair. The tools are being offered up for sale with COVID19 and Coronavirus discount codes to would-be cyber-attackers on the Darknet. There has also been a rise in the number of domains registered relating to Coronavirus and many of those domains, as you may have guessed, are malicious and likely to be used with phishing attacks. More details available from Checkpoint: https://blog.checkpoint.com/2020/03/19/covid-19-impact-as-retailers-close-their-doors-hackers-open-for-business/
- Many legitimate articles which have been posted on reputable sites about the Coronavirus contain comments sections that have been inundated with comment spamming attacks. The links followed from these articles seem like they lead to relevant, related information but the links instead actually lead to malware in various forms, including legitimate corona virus documents that have been embedded with malware. More information about this from Imperva: https://www.imperva.com/blog/concern-over-Coronavirus-leading-to-global-spread-of-fake-pharmacy-spam/
- A Coronavirus-themed phishing attack has been going around targeting the global shipping industry. The email comes with a subject “Coronavirus – Brief note for the shipping industry” and contains a word document attachment. This attachment contains an exploit for a 2.5 year old unpatched vulnerability that allows for installation of the AZORult malware. Users should always exercise extreme caution when opening attachments from unknown senders. Read more from Proofpoint: https://www.proofpoint.com/us/corporate-blog/post/Coronavirus-themed-attacks-target-global-shipping-concerns
- Another phishing campaign targeting Italian email addresses contained malicious Microsoft Office documents with embedded VBA macro containing the trickbot trojan. Trickbot is a banking trojan that can be used to steal victims’ confidential information and drop additional malware. The email subject line used in this campaign was “Coronavirus: informazioni importanti su precauzioni,” with the supposed author being “Dr. Penelope Marchetti,” an employee of the WHO in Italy. Read more from Digital Munition: https://www.digitalmunition.me/trickbot-campaign-targets-Coronavirus-fears-in-italy-sophos-news/
- A phishing campaign targeting Ukrainians contains a word document with a C# backdoor. Due to the inclusion of the text TrickyMouse threat researchers have dubbed the campaign TrickyMouse. They believe this is the work of the Hades APT. The document uses the branding and trademark of WHO and the Public Health Center of the Ministry of Health of Ukraine as a decoy and was used to target Ukraine. See origin tweet: https://twitter.com/RedDrip7/status/1230683740508000256?s=20
- A phishing campaign targeting Chinese citizens contained a subject line “Emergency Regulation Ordinance” containing a .RAR file that once opened would infect users with lokibot, exfiltrate their credentials, and contact a malicious IP address. See more from IBM X-force: https://exchange.xforce.ibmcloud.com/collection/62ed2dd58bbc189efd753918bef1bd05
- A phishing email pretending to come from the Centers for Disease Control containing the domains cdc-gov[.]org and cdcgov[.]org lead to a fake login portal designed to harvest Microsoft office credentials or to a page asking the user to donate bitcoin to the CDC to help develop a vaccine.
- A fake real-time Coronavirus tracking Android app, called “COVID19 Tracker,” was found to abuse user permissions to change the phone’s lock screen password and install CovidLock ransomware in return for a $100 bitcoin ransom. Installing unsupported application outside of the app store is dangerous and should not be done unless the source is trusted implicitly. Read more from DomainTools: https://www.domaintools.com/resources/blog/covidlock-mobile-Coronavirus-tracking-app-coughs-up-ransomware) and from Zscaler (https://www.zscaler.com/blogs/research/covidlock-android-ransomware-walkthrough-and-unlocking-routine
- A new spam campaign that aims to capitalize on the widespread mask shortage to trick recipients into paying for masks, only to send them nothing. Read more from F-Secure: https://blog.f-secure.com/Coronavirus-email-attacks-evolving-as-outbreak-spreads/
It is more important now than ever to educate users on good cybersecurity hygiene and to be hyper-vigilant to not fall for these Coronavirus themed scams and exploitation attempts. User training is an essential element to ensure the security of not just remote employees’ machines and networks but also to safeguard critical confidential company data. A phishing test provides data on which employees have been baited by the phishing email by clicking on the corresponding links. Your users can learn to identify suspicious emails, and in turn, apply security awareness best practices, by having the chance to experience a phishing attack. Atlas offers this service for our clients upon request.
