KryptoCibule – A Newly Discovered, Multitasking Cryptostealer
Researchers at ESET have discovered a new malware family they have code-named ‘KryptoCibule,’ with activity dating back to December of 2018. This malware is a high risk for organizations as it contains three threat capabilities: cryptomining, clipboard hijacking, and file exfiltration, while also deploying multiple techniques to avoid detection. KryptoCibule also makes extensive use of the Tor network and the BitTorrent protocol in its communication with C&C servers.
Written in C#, this malware also utilizes some legitimate software, such as Tor and the Transmission torrent client, both of which are bundled with the installer. Others, such as Apache httpd and the Buru SFTP server, are downloaded at runtime. The image below shows a general overview of the various components of this new malware and their interactions. The malware also contains a RAT functionality which, among other supported commands, allows for an EXEC command, allowing execution of arbitrary commands, and SHELL, which downloads a PowerShell script from its C&C. This script then loads a backdoor generated with the post-exploitation tool ‘Pupy.’
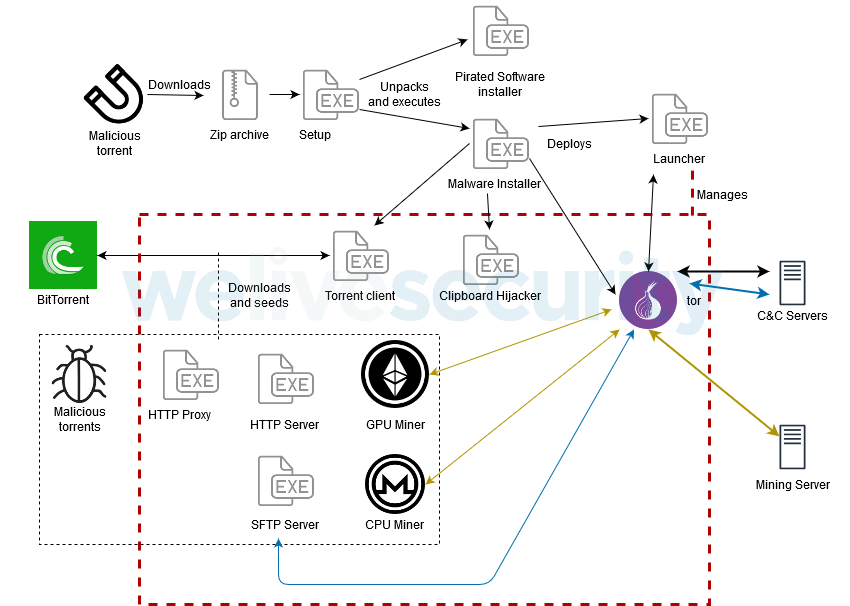
The malware is spread through malicious torrents for ZIP files, the contents of which are disguised as installers for cracked and pirated software and games. While the actual number of files may vary, there are five that are common to all KryptoCibule installer archives:
- packed.001
- packed.002
- Setup.exe
- Setup.dll
- packed.dat
packed.001 is the malware itself, while packed.002 is the installer for the expected software, both of which are XOR-encrypted with the keys contained in Setup.exe. When executed, Setup.exe decodes both the malware and the expected installer files. It then launches the malware in the background, and the expected installer in the foreground, thus giving the victim not indication that something is wrong. The malware will then continue to use the BitTorrent protocol to download updates and additional software; a hardcoded list of 50 trackers is used to get peers for all torrents. Victims are also used to seed both the torrents used by the malware and the malicious torrents that help spread it. Infected hosts get a list of magnet URIs, download them all and keep seeding them. This ensures that these files are widely available for others to download, which helps speed up the downloads and provides redundancy.
Utilizing a variety of ways to avoid detection, the original ZIP archive is obfuscated with the open source program ‘Obfuscar.’ This same tool is used on all the malware’s custom executables. The malicious code itself is located inside an XOR-encrypted file, with its key being a GUID hardcoded in the Setup.exe file. The malware is then installed to the hardcoded path %ProgramFiles(x86)%\Adobe\Acrobat Reader DC\Reader\update and uses legitimate Adobe Acrobat Reader executable names for the bundled Tor executable and its own. The malware then creates a scheduled task to be run every five minutes to achieve persistence. Before first executing its payload and on every iteration of the main loop, the malware performs a check for running analysis software using the following list. If any process with a matching name is found, it stops all running components and exits.
- cain
- filemon
- netmon
- netstat
- nmwifi
- perfmon
- processhacker
- procexp
- procexp64
- procmon
- regmon
- tasklist
- taskmgr
- tcpvcon
- tcpview
- wireshark
In terms of antivirus evasion, before initializing the cryptominer components, the malware performs a case-sensitive check of the rootSecurityCenter2\AntiVirusProduct WMI object for the strings avast, avg and eset. If any of these strings be detected, the cryptominer components will not be installed.
Whenever the malware installs itself, an update or a new component, the install path used is excluded from Windows Defender automatic. It also creates firewall rules to explicitly allow inbound and outbound traffic from its components using innocuous-looking names. A rule to block outbound traffic from the ESET Kernel Service (ekrn.exe) is also created.
In terms of the malware’s objectives, KryptoCibule has three components for obtaining cryptocurrencies from its victims. For cryptomining, the latest versions of KryptoCibule use ‘XMRig’, an open source program that mines Monero using the CPU, and ‘kawpowminer’, another open source program that mines Ethereum using the GPU. The second one is only used if a dedicated GPU is found on the host. Both of these programs are set up to connect to an operator-controlled mining server over the Tor proxy.
The second component masquerades as SystemArchitectureTranslation.exe. It uses the AddClipboardFormatListener function to monitor changes to the clipboard and to apply the replacement rules obtained from %C&C%/regexes to its content. These rules, in the form <regular_expresssion>!<wallet>, match the format of cryptocurrency wallet addresses and replace them with addresses of wallets controlled by the malware operator. This is an attempt to redirect transactions made by the victim to the operator’s wallets. This component uses a FileSystemWatcher to reload replacement rules whenever the settings.cfg file is changed.
The third component searches through the filesystem of each available drive and looks for filenames that contain certain terms. Most terms refer to cryptocurrencies, wallets or miners, but a few more generic ones like ‘crypto’, ‘seed’ and ‘password’ are present also. A few terms also correspond to paths or files that could provide other interesting data, ‘Desktop’, ‘private,’ including private keys ‘.ssh,’ ‘.aws.’ It gathers the full path of each of the matching files and sends the list to %C&C%/found/<unique name>.
Researchers believe that this works in tandem with the SFTP server running as an onion service on port 9187. This server creates mappings for every available drive and makes them available using credentials hardcoded in the malware. The gathered paths can thus be used for file exfiltration by having an attacker-controlled machine request them from the infected host over SFTP.
KryptoCibule also installs a legitimate Apache httpd server that is configured to act as a forward proxy without any restrictions and that is reachable as an onion service on port 9999.
Despite being around since 2018, this malware family is still considered new and hasn’t garnered much attention and it is still unclear how much cryptocurrency has actually been mined and stolen. See below for a full list of sources, as well as Indicators of Compromise.
Sources:
Indicators of Compromise (IOCs):
- SHA-1
- 3BCEF852639F85803974943FC34EFF2D6D7D916D
- armsvc.exe
- 352743EBE6A0638CC0614216AD000B6A43C4D46E
- SystemArchitectureTranslation.exe
- 70480D5F4CB10DE42DD2C863DDF57102BE6FA9E0
- Updater.exe
- 2E568CDF9B28824FBA1D7C16D8D0BE1D73A3FEBA
- Setup.exe
- 3BCEF852639F85803974943FC34EFF2D6D7D916D
- Network
- rlwryismmgjijryr55u5rqlbqghqvrwxe5qgxupuviyysxkky5wah6yd.onion
- 4dtu3lxrpx6nn7snjovoc3ldiy4x67k7qsrgzftvkrttoqbwnsuirhqd.onion
- v6lajszeqfkt3h2nptorindpf3mow5p3thrx2vuqbqzbv3tjrcqmgdqd.onion
- Scheduled Tasks
- GoogleUpdateTask
- %LocalAppData%\Microsoft\Architecture\SystemArchitectureTranslation.exe
- Adobe Update Task
- %ProgramFiles(X86)%\Adobe\Acrobat Reader DC\Reader\Update\armsvc.exe
- GoogleUpdateTask
