DeathStalker – Possible ‘For-Hire’ Mercenary APT
DeathStalker is an APT with activities dating back to at least 2018 and possibly as far back as 2012. They exist as an anomaly in the cyber-security field as their goal is not the distribution of ransomware, the gathering of payment information for later resell, or any of the other “typical” activities performed by other well-known APTs. Instead, DeathStalker focuses on the gathering of sensitive business information, leading many researchers to believe that DeathStalker is actually a group of mercenaries offering their hacking skills as a for-hire service. Their current tool of choice is a PowerShell-based implant called ‘PowerSing,’ which is distributed through LNK files contained in archives delievered through spear-phishing.
Once downloaded and executed by the victim, PowerSing has two tasks:
- Capturing periodic screenshots from the victim’s machine, which are then sent to the C&C server
- Execution of arbitrary PowerShell scripts provided by the C&C
But what makes PowerSing truly powerful is that its true goal is to establish a foothold on the victim’s machine and network to enable the projection of further tools. DeathStalker also utilizes various public services as ‘dead drop resolvers’ in order to provide PowerSing the IP address for its C&C servers. These services provide a way for attackers to store data at a fixed URL through public posts, comments, user profiles, content descriptions, etc. Messages left by the attackers follow the following patterns: “My keyboard doesn’t work… [string].” and “Yo bro I sing [Base64 encoded string] yeah”.
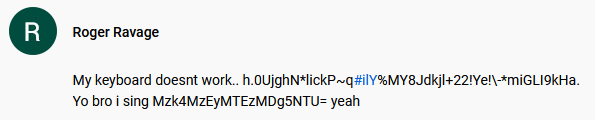
During their investigation, SecureList was able to discover such messages on:
- Google+
- Imgur
- ShockChan
- Tumblr
- YouTube
- WordPress
When first executed, PowerSing will connect to any dead drop receiver coded into it and retrieves the previously mentioned string (e.g. the comment/user profile/content description/etc.) Its first stage will then process the first string of these messages, which contain the AES key used to then decode stage two. Stage two then connects to the dead drop again to obtain the integer encoded in the second string, and then will divide the integer by an arbitrary constant, which varies depending on the sample, before being converted into an IP address. This address is then stored on the victim’s hard drive and is used to establish a connection to the real C&C server.
This reliance on public services allow the attacker to blend initial backdoor communications into legitimate network traffic but this also serves to limit what potential victims can do to defend against this type of hidden communication, as services often cannot be blacklisted at the company level, and getting content taken down from them can be a difficult process. The utilization of these public dead drops also prevents the attacker fully remove all traces of their activities since these public services are often indexed or archived. Its thanks to the indexed data and internet archives that SecureList believes that PowerSing was first used in August of 2017.
PowerSing is not the only tool that DeathStalker has links to. Both Janicab, a malware family first discovered in 2012, and Evilnum, discovered in July of 2019, are scripting language-based toolchains that exhibit similarities to PowerSing, thus leading researchers to believe that all three, PowerSing, Janicab, and Evilnum, are all operated by the same group. These similarities are:
- All three are distributed through LNK files contained in archives delivered through spear-phishing
- They obtain C&C information from dead drop resolvers using regular expressions and hardcoded sentences
- IP addresses are obtained in the form of integers that are then divided by a hardcoded constant before being converted
- Minor code overlaps between the three malware families could indicate that they’ve been developed by the same team, or inside a group that shares software development practices
- The three malware families all have screenshot capture capabilities.
- The goal of both PowerSing and Evilnum tend to be of a corporate espionage nature, although of different industries
DeathStalker primarily targets private entities within the financial sector, such as law offices, financial consultancy firms, financial technology companies, and the like. SecureList has identified PowerSing-related activities in Argentina, China, Cyprus, Israel, Lebanon, Switzerland, Taiwan, Turkey, the UK, and the UAE. Evilnum has targeted victims in Cyprus, India, Lebanon, Russia, Jordan, and the UAE.
It’s believed that DeathStalker chooses its targets based purely on their perceived value or through customer requests. It’s possible that any company in the financial sector could be targeted by DeathStalker, despite its geographical location.
Sources:
Indicators of Compromise (IOCs):
- File Hashes
- D330F1945A39CEB78B716C21B6BE5D82 Malicious LNK
- D83F933B2A6C307E17438749EDA29F02 Malicious LNK
- 540BC05130424301A8F0543E0240DF1D Malicious LNK
- 3B359A0E279C4E8C5B781E0518320B46 Malicious LNK
- 6F965640BC609F9C5B7FEA181A2A83CA Malicious LNK
- E1718289718792651FA401C945C17079 Malicious LNK
- F558E216CD3FB6C23696240A8C6306AC Malicious LNK
- B38D1C18CBCCDDDBF56FDD28E5E6ECBB Loader Script
- E132C596857892AC41249B90EA6934C1 PowerSing Stage 1
- 9A0F56CDACCE40D7039923551EAB241B PowerSing Stage 1
- 0CEBEB05362C0A5665E7320431CD115A PowerSing Stage 1
- C5416D454C4A2926CA6128E895224981 PowerSing Stage 1
- DBD966532772DC518D818A3AB6830DA9 PowerSing Stage 1
- B7BBA5E70DC7362AA00910443FB6CD58 PowerSing Stage 1
- 2BE3E8024D5DD4EB9F7ED45E4393992D PowerSing Stage 1
- 83D5A68BE66A66A5AB27E309D6D6ECD1 PowerSing Stage 1
- 50D763EFC1BE165B7DB3AB5D00FFACD8 PowerSing Stage 1
- C&C Servers
- 54.38.192.174
- 91.229.76.17
- 91.229.76.153
- 91.229.77.240
- 91.229.77.120
- 91.229.79.120
- 54.38.192.174
- 105.104.10.115
